Two-Factor Login With One-Time SMS Code – A Developer’s How-To Guide
In this how-to guide for developers, we will show you, step-by-step, how easy it is to set up SMS two-factor authentication with GatewayAPI. If you’re not already a user, don’t worry, you can sign up for free here!
One way to make your authentication process more secure is by adding in more authentication factors. One such factor, which is widely used due to its convenience, is a one-time SMS code. This is sent to the account owners’ phone number when, and only when, a valid password has been entered. And only by typing in that extra one-time code, can the user be authenticated. This is known as SMS two-factor authentication or as an SMS password, SMS passcode, or OneCode, and can be provided by Authy and similar services.
By using GatewayAPI and a couple of neat libraries, it is straightforward to implement this additional factor, and right here we’re going to show you how!
Connecting to the API
Before we can start authenticating account owners using a two-factor process, we need to know how to send an SMS using GatewayAPI in the first place. (If you are not registered as a GatewayAPI customer yet, you can easily set up your account here!)
In this post, we will be using Python for the code examples. For Ruby and PHP developers, we have examples in our documentation for using GatewayAPI with those and many other languages.
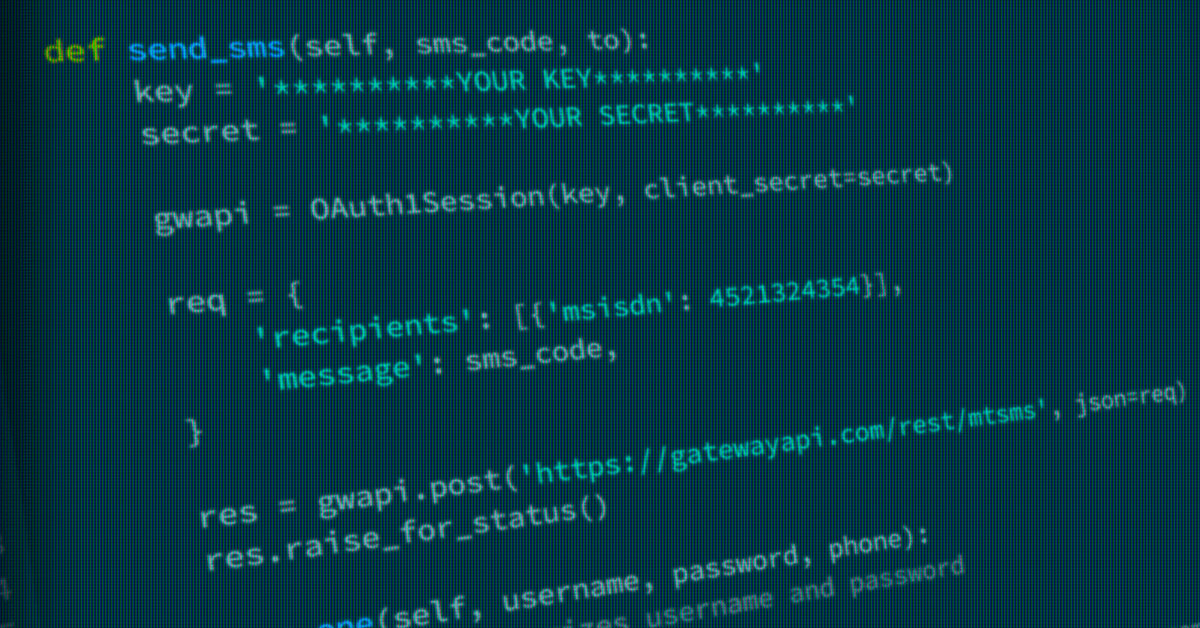
GatewayAPI has a couple of ways to authenticate. We will focus on using OAuth1 since it is both supported and straightforward.
Go to your dashboard and in the sidebar choose settings -> OAuth keys. There should already exist a key-set, with a label saying it was created by the system. Click on the key-button on the right and you will be presented with your key and secret. These are what you will use to authenticate with the API.
Sending an SMS is now straightforward. Using Python it can be done like so:
Install dependencies with: pip install requests_oauthlib
You can find examples on how to sent a SMS using more languages in our documentation.
Setting up SMS two-factor authentication
Now we know how to send a text, we can move on to the next stage, setting up SMS two-factor authentication.
To reiterate, this two-factor process includes two steps, the first is authenticating with a username and password, and if that succeeds, the second step is authenticating with a one-time code that will be sent to you as an SMS using GatewayAPI’s Rest API.
Since it is a two-factor process, we need a way to store some data between the two steps. For this we will use a Redis server, but it could be a session object, a MySQL database or any other way to store state between the two steps.
We also use PyOTP, which is a library that among other things makes it easy to make one-time passwords. For Ruby developers there is a library similar to PyOTP called ROTP. For PHP developers there is OTPHP.
What happens next through GatewayAPI?
Step one
We will create an AuthClient, which will do all the heavy lifting for us.
We use a counter in our Redis database that increments for each authentication attempt for that particular user. This count will be seeded to our PyOTP instance to ensure uniqueness. We then acquire a new code from PyOTP. We use this to authenticate the SMS code in the second step. We then send off the SMS code to the users’ phone number using a function that is almost identical to our previous SMS-sending example. Lastly, we return the ID of the user that matched the username and password.
Safety first!
We store a random secret for each user on demand in Redis, but you can generate and store this secret in any way you like, just make sure it’s secure. More on management of secrets.
Step two
Step two is even simpler. We provide the obtained user_id that was returned from step_one and the SMS code that was sent to the users’ phone number. We look up the current counter in our Redis and make sure the SMS code matches.
Using all of this our flow in code could look something like this for step one:
And for step two:
If the authentication is a success, the user was authenticated using a two-factor process, and an authentication token was obtained.
The example code is focused on showcasing the technique of using GatewayAPI and how to use one-time passwords. In a production setting, modern security measures such as brute-force prevention and encryption of all sensitive data should be applied to your solution to fend off attackers. Take a look at RFC4226s consideration section for what you should be wary of when using PyOTP or similar libraries and techniques.
There are many possibilities when including SMS in your applications. SMS two-factor authentication consisting of a password and an SMS code is only one of them. With our easy and convenient APIs, it is easy to make your authentication processes more secure without making it complicated for all of your SMS-receiving users.
Code example
We have included the full client for the examples in Python as a reference, but in any case, customization will be needed for your solution.
Python AuthClient
Global SMS Gateway
We have made it simple to implement SMS services into your business! We offer some of the lowest prices in the world, easy integration, world-class customer support, an intuitive interface, and a rock-solid uptime of over 99.99%. If you don’t have an account yet, you can create a FREE account in less than two minutes! Simply go to GatewayAPI or contact sales@gatewayapi.com.
If you have a concept or business that could benefit from employing SMS communication, contact us. We will help you get started, contact us today!

